It happened like it happens so many times on a daily basis. "Yes, you see, I took my company issued laptop home. Yes, and I got an e-mail from someone I trust, and it had an attachment, and I clicked on it. When the attachment just wouldn't open, I realized I had done something wrong. Oh, the e-mail? Yeah, no, it wasn't corporate e-mail. I was checking my personal e-mail. I was at home!"
The, attachment, in this case, was very succinctly named "Docx.jar". Now, as a novice in the arena of malware analysis, I like .JAR files, because all I need to do is dump them into JD-Gui and start rummaging through code. However, before we do that, let's at least get the footwork out of the way.
Filename: Docx.jarSize: 212Kb
MD5: ab3e11b7a5fd924be74d3d737fddb9f8
Basic file information. That having been said, let's get right to it!
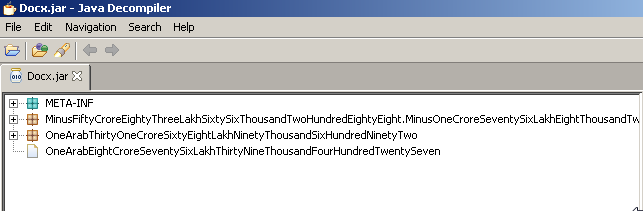
The first thing I did, as previously stated, was open the .JAR file in JD-Gui.
Those are some wonderfully obfuscated class names right there. However, the class names are not really what drew my interest. That was all in the META-INF > MANIFEST.MF section:
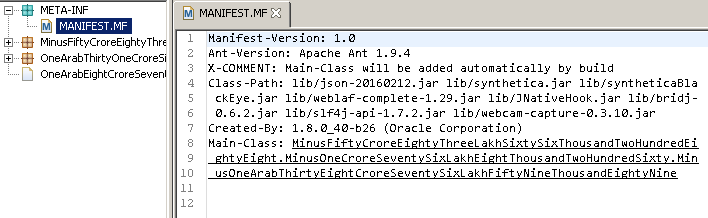
So, I have taken the liberty of researching each of these libraries and summarizing them below:
lib/json-20160212.jarThis is json. Not a whole lot more to say other than that, but if you want a description: "JSON is a light-weight, language independent, data interchange format." Also, as of this writing, this is the current version of JSON, so we know the malware sample can't be any older than 2 months, again as of this writing.
Reference: http://mvnrepository.com/artifact/org.json/json/20160212
lib/synthetica.jar"Synthetica is a Look and Feel for Swing and is based on Synth which is part of the Java Platform version 1.5. Synthetica provides many different looks through Themes for the core components of Swing with rounded borders, shadowed popup menus and nice icons. Moreover it enables you to modify existing Themes and to create your own look and feel only by editing a XML-based configuration file - you don't have to write complex Java-GUI-Code." So, this is used for making the GUI component of the malware (as seen by the attacker) appear as desired.
Reference: http://www.javasoft.de/synthetica/
lib/syntheticaBlackEye.jarThis is a theme for Synthetica. So, this is what the GUI will look like to the attacker. The reference website has screenshots and a demo.
Reference: http://www.javasoft.de/synthetica/themes/
lib/weblaf-complete-1.29.jar"Java Look and Feel for cross-platform Swing applications." So, more GUI stuff. Enough said.
Reference: http://weblookandfeel.com/
lib/JNativeHook.jar"Global keyboard and mouse listeners for Java." Okay, now we are getting into the meat of things here. If I had to take a guess, I'd say we are spying on keyboard and mouse actions.
Reference: https://github.com/kwhat/jnativehook
lib/bridj-0.6.2.jar"BridJ aims to be the ultimate Java / native interoperability library (BSD-licensed). Call C, C++, ObjectiveC libraries without compiling native code." Again, just conjecture here, but this should let us reach a little more deeply into the OS itself, rather than relying solely on outside Java code.
Reference: https://code.google.com/archive/p/bridj/
lib/slf4j-api-1.7.2.jar"The Simple Logging Facade for Java (SLF4J) serves as a simple facade or abstraction for various logging frameworks (e.g. java.util.logging, logback, log4j) allowing the end user to plug in the desired logging framework at deployment time." Gonna guess that this will be used to feed verbose data back to attacker.
Reference: http://www.slf4j.org/
lib/webcam-capture-0.3.10.jar"This library allows you to use your build-in or external webcam directly from Java. It's designed to abstract commonly used camera features and support multiple capturing farmeworks." Scary beyond reason, but also fairly obvious.
Reference: http://webcam-capture.sarxos.pl/
So, if it wasn't already painfully obvious, this malware is a spying utility. It can access the webcam, as well as perform mouse/keyboard logging. From the attackers side, they will see a nice web GUI from which they can spy on their targets.
NOTE: When I initially started looking at this in my office's VM, I could've sworn that I saw a library that dealt with microphone/audio hooking, but I haven't been able to confirm that while analyzing at home.
I didn't dig any further into the source code, mostly because it was too obfuscated for my nascent skillset to handle. I did, however, have a basic idea of what the malware would do, so it seemed the time to switch over to dynamic analysis mode.
So, I first did some diffing, then I did some packet captures. But, before we even go that far, let's look at what happened when I opened the command line and just launched the malware:
C:\Users\Malware Inspector\Desktop\Samples\Samples\Downloads>java -jar Docx.jarMain-Class : qua.quaverse.qarallax.Bismillahirrahmanirrahim
slave
MinusFiftyCroreEightyThreeLakhSixtySixThousandTwoHundredEightyEight.MinusOneCror
eSeventySixLakhEightThousandTwoHundredSixty.OneArabNinetyEightCroreNinetySevenLa
khSixtyThousandSixHundredThirtyFive Error for Resource : embedding
Looking for Resource on Linked : sun.misc.Launcher.AppClassLoader
id=72000000095 to_id=71000000095
C:\Users\Malware Inspector\Desktop\Samples\Samples\Downloads\Docx.jar
C:\Users\Malware Inspector\.3ojHSEnbdL\Q5Dn8.1H8FbR9Is0x\c6x84fwpDqN9EMt3c\XvBa_
_DMv6TPoRppl.jar
Downloading Library: http://lib.qarallax.com/qarallax-lib/bridj/bridj-0.6.2.jar
=> C:\Users\MALWAR~1\AppData\Local\Temp\1664903225628141467460795952903701664903
2279860 => C:\Users\Malware Inspector\.3ojHSEnbdL\Q5Dn8.1H8FbR9Is0x\c6x84fwpDqN9
EMt3c\lib\bridj-0.6.2.jar
Done.
Downloading Library: http://lib.qarallax.com/qarallax-lib/slf4j/slf4j-api-1.7.2.
jar => C:\Users\MALWAR~1\AppData\Local\Temp\166502376151971210550982508354760166
50237642460 => C:\Users\Malware Inspector\.3ojHSEnbdL\Q5Dn8.1H8FbR9Is0x\c6x84fwp
DqN9EMt3c\lib\slf4j-api-1.7.2.jar
Done.
Downloading Library: http://lib.qarallax.com/qarallax-lib/webcam/webcam-capture-
0.3.10.jar => C:\Users\MALWAR~1\AppData\Local\Temp\16650368914530208876014234498
671816650368931477 => C:\Users\Malware Inspector\.3ojHSEnbdL\Q5Dn8.1H8FbR9Is0x\c
6x84fwpDqN9EMt3c\lib\webcam-capture-0.3.10.jar
Done.
Downloading Library: http://lib.qarallax.com/qarallax-lib/json/json-20160212.jar
=> C:\Users\MALWAR~1\AppData\Local\Temp\166506227099993837444470750942358166506
22728788 => C:\Users\Malware Inspector\.3ojHSEnbdL\Q5Dn8.1H8FbR9Is0x\c6x84fwpDqN
9EMt3c\lib\json-20160212.jar
Done.
Downloading Library: http://lib.qarallax.com/qarallax-lib/jnhook/JNativeHook.jar
=> C:\Users\MALWAR~1\AppData\Local\Temp\166507268013941068474720167227991166507
26818341 => C:\Users\Malware Inspector\.3ojHSEnbdL\Q5Dn8.1H8FbR9Is0x\c6x84fwpDqN
9EMt3c\lib\JNativeHook.jar
Done.
So, despite ALL of that obfuscation effort, I now see where the library files are being downloaded from. First, let's get some info on that host!
Grabbed the WHOIS information for the host, and here is what we get:
Domain Name: QARALLAX.COMRegistry Domain ID : 2002157315_DOMAIN_COM-VRSN
Registrar WHOIS Server : http://whois.nicproxy.com
Registrar URL: http://www.nicproxy.com
Updated Date: 2016-04-23T08:02:50Z
Creation Date: 2016-02-12T09:44:30Z
Registrar Registration Expiration Date: 2017-02-12T09:44:30Z
Registrar:NICS TELEKOMUNIKASYON TICARET LTD.STI.
Registrar IANA ID: 1454
Registrar Abuse Contact Email: abuse@nicproxy.com
Registrar Abuse Contact Phone: +90.2122132963
Reseller: NATRO COMMUNICATION LTD.
Domain Status: ok http://www.icann.org/epp#OK
Registry Registrant ID: CID-901373.G3Z7E1G2
Registrant Name: NicProxy Customer
Registrant Organization: Whois Privacy Protection Service.
Registrant Street: Elif Sok. No 4
Registrant City: Istanbul
Registrant State / Province: Sisli
Registrant Postal Code: 34394
Registrant Country: TR
Registrant Phone: +90.2122132963
Registrant Phone Ext:
Registrant Fax: +90.2122132963
Registrant Fax Ext:
Registrant Email: 901373.g3z7e1g2@nicproxy-customer.com
Registry Admin ID: CID-901373.G3Z7E1G2
Admin Name: NicProxy Customer
Admin Organization: Whois Privacy Protection Service.
Admin Street: Elif Sok. No 4
Admin City: Istanbul
Admin State / Province: Sisli
Admin Postal Code: 34394
Admin Country: TR
Admin Phone: +90.2122132963
Admin Phone Ext:
Admin Fax: +90.2122132963
Admin Fax Ext:
Admin Email: 901373.g3z7e1g2@nicproxy-customer.com
Registry Tech ID: CID-901373.G3Z7E1G2
Tech Name: NicProxy Customer
Tech Organization: Whois Privacy Protection Service.
Tech Street: Elif Sok. No 4
Tech City: Istanbul
Tech State / Province: Sisli
Tech Postal Code: 34394
Tech Country: TR
Tech Phone: +90.2122132963
Tech Phone Ext:
Tech Fax: +90.2122132963
Tech Fax Ext:
Tech Email: 901373.g3z7e1g2@nicproxy-customer.com
Name Server: NS1.DIGITALOCEAN.COM
Name Server: NS2.DIGITALOCEAN.COM
DNSSEC: Unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
Also, we can see that the IP address is 104.236.159.161, and the website title is "Jrypter | Jrypt it!"
Did a quick Google on that site name, and it turns out Jrypter is a "Java binary crypter", according to their website. It also claims to be provided by QUAverse. So, I performed another Google query, and we see that:
"Quaverse RAT or QRAT is a fairly new Remote Access Tool (RAT) introduced in May 2015. This RAT is marketed as an undetectable Java RAT. As you might expect from a RAT, the tool is capable of grabbing passwords, key logging and browsing files on the victim's computer...
...Attached to it was a .zip attachment containing an executable .JAR file." (source: https://www.trustwave.com/Resources/SpiderLabs-Blog/Quaverse-RAT--Remote-Access-as-a-Service/)
Well, that is starting to sound very familiar, I'd say. But, I don't want to call it a day just because I think I found the malware family to which this file belongs. That isn't very fun, nor does it teach me anything.
So, interestingly enough, the path to which the files are dropped are the same in my test environment as they were when I discovered the malware initially on the victim's machine. Files are dropped to "C:\Users\{USERNAME}\.3ojHSEnbdL" and additional subdirectories.
At this point, a startup entry is created as well:
"C:\Program Files\Java\jre1.8.0_77\bin\java" -jar "C:\Users\Malware Inspector\.3ojHSEnbdL\Q5Dn8.1H8FbR9Is0x\c6x84fwpDqN9EMt3c\XvBa__DMv6TPoRppl.jar"That file "XvBa__DMv6TPoRppl.jar" is just "Docx.jar" again. At this point, I started looking at network traffic to/from my machine, and I noted this in CurrPorts:
java.exe 2956 TCP 50989 10.0.2.15 1714 85.17.30.134 ersey.eurodyley.com Established C:\Program Files\Java\jre1.8.0_77\bin\java.exeSo, there is our established connection to the malware's server over port 1714. Time to perform another host lookup!
Domain Name: eurodyley.comRegistry Domain ID: 1968501325_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.register.com
Registrar URL: http://www.register.com
Updated Date: 2015-10-14T15:33:47Z
Creation Date: 2015-10-14T15:33:46Z
Registrar Registration Expiration Date: 2016-10-14T15:33:46Z
Registrar: Register.com, Inc.
Registrar IANA ID: 9
Registrar Abuse Contact Email: abuse@web.com
Registrar Abuse Contact Phone: +1.8773812449
Reseller:
Domain Status: clientTransferProhibited http://icann.org/epp#clientTransferProhibited
Registry Registrant ID:
Registrant Name: Genenergy Padicious
Registrant Organization:
Registrant Street: 848 N. Rainbow Road #8001
Registrant City: Las Vegas
Registrant State/Province: NV
Registrant Postal Code: 89107
Registrant Country: US
Registrant Phone: +1.7754326453
Registrant Phone Ext.:
Registrant Fax:
Registrant Fax Ext.:
Registrant Email: server247@matilogicully.net
Registry Admin ID:
Admin Name: Genenergy Padicious
Admin Organization:
Admin Street: 848 N. Rainbow Road #8001
Admin City: Las Vegas
Admin State/Province: NV
Admin Postal Code: 89107
Admin Country: US
Admin Phone: +1.7754326453
Admin Phone Ext.:
Admin Fax:
Admin Fax Ext.:
Admin Email: server247@matilogicully.net
Registry Tech ID:
Tech Name: Genenergy Padicious
Tech Organization:
Tech Street: 848 N. Rainbow Road #8001
Tech City: Las Vegas
Tech State/Province: NV
Tech Postal Code: 89107
Tech Country: US
Tech Phone: +1.7754326453
Tech Phone Ext.:
Tech Fax:
Tech Fax Ext.:
Tech Email: server247@matilogicully.net
Name Server: dns2.register.com
Name Server: dns1.register.com
DNSSEC: Unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
The IP address is 83.149.125.235. Now, I will NOT port scan an IP address I do not own nor do not have written permission to scan, but I can see if the IP address has ever been hit by one of Shodan's scanners. Unfortunately, it had not been hit by Shodan, but the original IP address that was listed in my packet captures (so, where the host lived on 04/15/2016) was 85.17.30.134, and that had been hit by Shodan:
22 - SSH25 - SMTP
53 - DNS
80 - HTTP
110 - POP3
143 - IMAP
465 - SMTPS
587 - SMTP
993 - IMAP-SSL
995 - POP3-SSL
3306 - MySQL
All common ports, but I did not see that 1714 port listed anywhere, which is a shame.
Dug through my packet captures with Wireshark and Network Miner, but the traffic is encrypted, so couldn't get much deeper at this step.
Now, I did go ahead and run wget against the first host we encountered, and I managed to pull down a bit more than just the original library files:
syshook/system-hook-2.2"Global Keyboard / Mouse Hook for Java applications."
Reference: https://github.com/kristian/system-hook/releases
sql/sqlite-jdbc-3.8.11.2.jar"SQLite JDBC, developed by Taro L. Saito, is a library for accessing and creating SQLite database files in Java."
Reference: https://bitbucket.org/xerial/sqlite-jdbc
jna/jna.jar, jna-platform.jar"JNA provides Java programs easy access to native shared libraries without writing anything but Java code - no JNI or native code is required. This functionality is comparable to Windows' Platform/Invoke and Python's ctypes"
Reference: https://github.com/java-native-access/jna
dumper/laz.qrc, outdmp.qrc, wtfdmp.qrcNOTE: Had to tackle these a bit differently. Despite them all having the same extension, taking a look at the magic numbers for each file (or running them through trid) revealed that they were actually 2 executables and a zip archive file, respectively within the list.
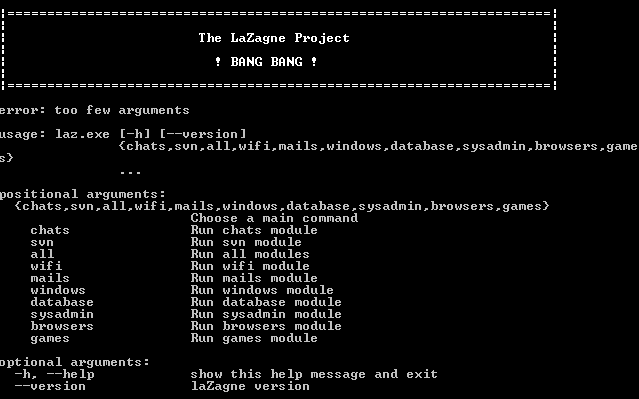
laz.qrc => laz.exeOnce this file was renamed, I just launched it via command line and got the below result; I looked up the LaZagne project, and it is a one-stop application for dumping credentials from various applications:
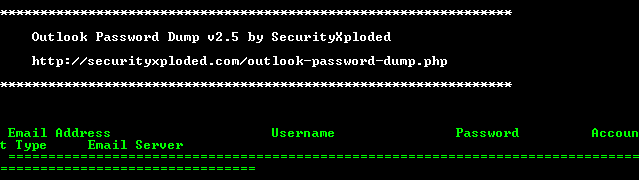
outdmp.qrc => outdmp.exeI recognized the icon for this file, and running it via command line confirmed that it was Outlook Password Dump by Security Xploded:
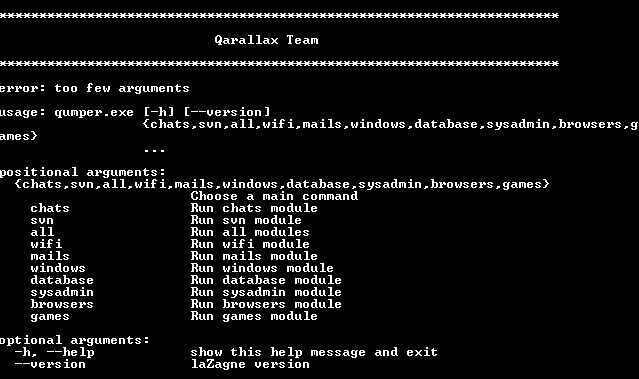
wtfdmp.qrc => wtfdump.zipHad to unzip this file first, but once I did I saw an executable named "qumper.exe". Ran it in command line. This looks exactly the LaZagne project except with a custom banner:
Truthfully, that is where my analysis ends. Seems we have a multi-faceted spying tool that has a range of capabilities, though I am not sure all of them are being employed by the attackers as of yet, or at least not with the dropper I encountered. I may come back and edit this post if I gain more information afterward.
Thanks for reading, as always, and remember to stay safe out there. You never know what risk you may be exposed to at any given time!