Hello!
It's been a long time. Long-overdue status updates and site upgrades are in the works, but as I was working on them I got involved in an attack that I couldn't resist sharing.
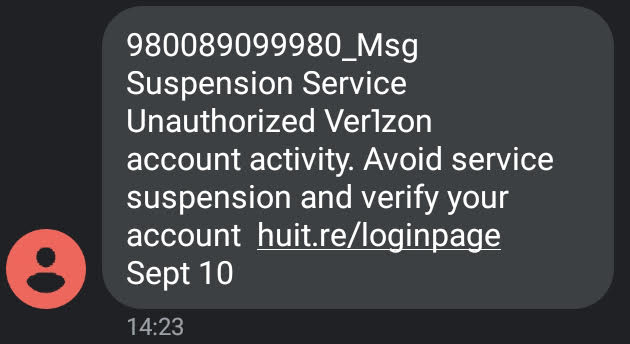
For the first time in at least a couple of years I received a SMiSh message. The message purported to come from Verizon Wireless, but the link was clearly not Verizon.
Low-effort SMiSh spotted, right out of the gate.
As it turns out, hxxp://huit[.]re is a URL shortener. Off to my favorite URL Expander (https://urlex.org/) service, which revealed that the full URL was hxxp://200[.]192[.]246[.]82:8081/index.php?r=verify. Once inside my sandbox, I visited the site.
I'd give them a D- at best.
I grabbed the HTML of this page, but there was nothing particularly interesting happening inside. I had kicked off and was watching in Fiddler for anything unexpected as well, but nothing exciting took place. I entered one of my testing e-mail addresses and submitted the form.
The next page asked for my password. I helpfully provided a fraudulent one, noting it down so I can look for it in future data breaches. Again, nothing interesting happened.
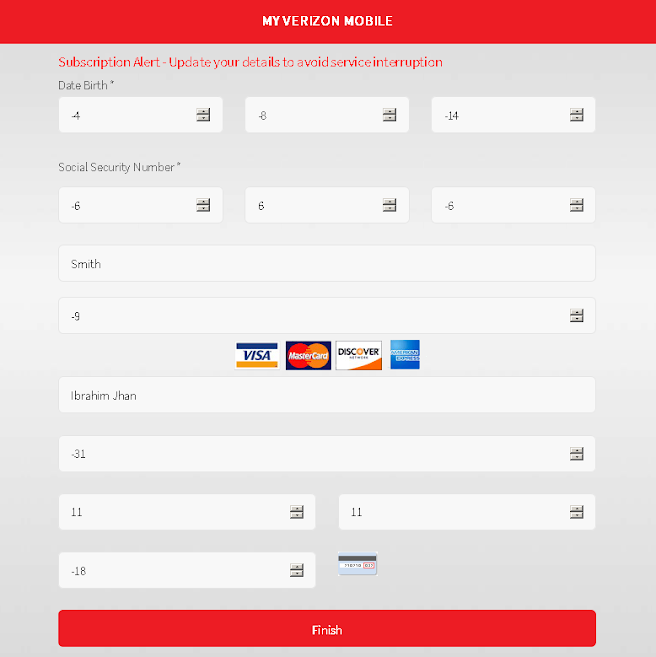
Finally, we've reached the meatiest part of this shallow rabbit hole. As you can see in the below image, a veritable cornucopia of information was requested on this page. The best part about this page, however, was the incremental arrow selectors for each text box. Par for my whimsical spirit, I entered a load of nonsense into all of the boxes.
The chuckles I got from this alone have made the analysis worth it.
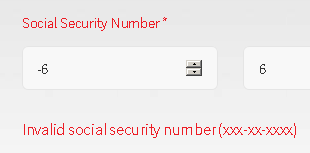
I submitted my answers, but unfortunately I was told that my SSN was invalid. I entered a SSN in valid format (I tried straight 0's and an SSN in the range deemed by the Social Security Administration as invalid), but I received the same message. I tried it both with and without hyphens, but that did not seem to make a difference. All of my SSN attempts were rejected as invalid, but none of the other fields seemed to matter to the supposed error checking occurring on this page. This led me to believe that either the site didn't care about any other piece of data (unlikely, as every single one of those fields would be a juicy prize for an attacker), or the attacker in question was simply too lazy to do anything beyond this page and has already siphoned off the details, leaving the victim in an unresolvable faux error Hell.
Sure, -31 is a valid credit card number but you're going to yell at me for an invalid SSN.
The HTML for this page supported my latter theory, as the only field with any sort of error correction other than "cannot be blank" was the SSN field. HTML for the post-invalid SSN page was uninteresting as well. However, here's where my path diverges for a bit.
I tried to manually browse back to a previous page to test something, and I ended up at an error page. It contained a lot of legitimate links to the actual Verizon site, but in reviewing the HTML I noted a link to /sitemap.jsp. I tried to visit this page, but was told it did not exist. On this error page was displayed some server details, as shown below:
Apache/2.4.10 (Win32)OpenSSL/1.0.1h
PHP/5.4.31
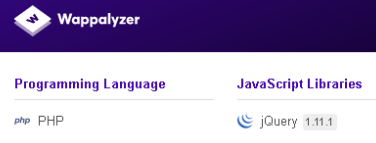
And here's Wappalyzer output just for posterity's sake:
So, we've browsed through all of the pages we can, it seems. That means it's time for some digging into additional files (CSS, JS, etc.) I already had the files I had collected as I visited each page, but for the sake of completion I fired up wget and nabbed everything that way, too.
Here's a list of all the files I grabbed along with any notable info extracted from each:
1. jquery.min.js
/*! jQuery v1.8.3 jquery[.]com | jquery[.]org/license */I'm pointing this out because the version listed in this file does not match Wappalyzer's output. More on that later.
2. jquery.yiiactiveform.js
* jQuery yiiactiveform plugin file.*
* @author Qiang Xue
* @link hxxp://www[.]yiiframework[.]com/
* @copyright Copyright © 2008-2010 Yii Software LLC
* @license hxxp://www[.]yiiframework[.]com/license/
* @since 1.1.1
Just taking inventory of all the pieces involved here.
3. overlay.png
File Modification Date/Time : 2015:05:09 13:30:12-04:00XMP Toolkit : Adobe XMP Core 5.3-c011 66.145661, 2012/02/06-14:56:27
Original Document ID : xmp.did:3CDCB2821330E41184A4A433B6FDD16D
Document ID : xmp.did:FB92684930A711E49DC7DAC82C1CF299
Instance ID : xmp.iid:FB92684830A711E49DC7DAC82C1CF299
Creator Tool : Adobe Photoshop CS6 (Windows)
Derived From Instance ID : xmp.iid:3EDCB2821330E41184A4A433B6FDD16D
Derived From Document ID : xmp.did:3CDCB2821330E41184A4A433B6FDD16D
I was fascinated by the file modification date here, though I know well enough it could be completely fraudulent. I kept the remainder of the details for archival purposes.
4. font-awesome.min.css
/*!* Font Awesome 4.2.0 by @davegandy - hxxp://fontawesome[.]io - @fontawesome
* License - hxxp://fontawesome[.]io/license (Font: SIL OFL 1.1, CSS: MIT License)
*/
@font-face {
font-family: 'FontAwesome';
src: url('../fonts/fontawesome-webfont.eot?v=4.2.0');
src: url('../fonts/fontawesome-webfont.eot?#iefix&v=4.2.0') format('embedded-opentype'), url('../fonts/fontawesome-webfont.woff?v=4.2.0') format('woff'), url('../fonts/fontawesome-webfont.ttf?v=4.2.0') format('truetype'), url('../fonts/fontawesome-webfont.svg?v=4.2.0#fontawesomeregular') format('svg');
font-weight: normal;
font-style: normal
}
Still inventorying.
5. skel.css
/* Resets (hxxp://meyerweb[.]com/eric/tools/css/reset/ | v2.0 | 20110126 | License: none (public domain)) */More inventory.
6. style.css
@import url(font-awesome.min.css);/p>@import url("hxxp://fonts[.]googleapis[.]com/css?family=Source+Sans+Pro:300,400,300italic,400italic");
/*
Alpha by ODDW
html5css3 | @n33co
*/
As you will see below, the attacker really likes abusing @n33co's products.
7. style-wide.css
/*Alpha by HTML5 UP
html5up[.]net | @n33co
Free for personal and commercial use under the CCA 3.0 license (html5up[.]net/license)
*/
More @n33co, but a different product.
8. background.jpg
File Modification Date/Time : 2016:01:16 20:38:52-05:00Software : Adobe Photoshop CS3 Windows
Modify Date : 2016:01:17 12:38:49
Slices Group Name : Untitled-2
Writer Name : Adobe Photoshop
Reader Name : Adobe Photoshop CS3
XMP Toolkit : Adobe XMP Core 4.1-c036 46.276720, Mon Feb 19 2007 22:40:08
Creator Tool : Adobe Photoshop CS3 Windows
Create Date : 2016:01:17 12:38:49+08:00
Metadata Date : 2016:01:17 12:38:49+08:00
Document ID : uuid:EFC8A121D4BCE5118124BF4D7519941D
Instance ID : uuid:F0C8A121D4BCE5118124BF4D7519941D
Native Digest : 256,257,258,259,262,274,277,284,530,531,282,28 3,296,301,318,319,529,532,306,270,271,272,305,315,33432;3C4A50216E4F814446990CFA 33EFD58C
Derived From Instance ID : uuid:EEC8A121D4BCE5118124BF4D7519941D
Derived From Document ID : uuid:EEC8A121D4BCE5118124BF4D7519941D
Profile CMM Type : Linotronic
Primary Platform : Microsoft Corporation
Device Manufacturer : Hewlett-Packard
Profile Creator : Hewlett-Packard
Profile Copyright : Copyright (c) 1998 Hewlett-Packard Company
Device Mfg Desc : IEC hxxp://www[.]iec[.]ch
Device Model Desc : IEC 61966-2.1 Default RGB colour space - sRGB
Another interesting modification date. The rest is recorded for historical purposes.
9. init.js
/*Alpha by ODDW
html5upCss3 | @n33co
*/
And here we have @n33co again with a third product.
10. jquery.dropotron.min.js
/* jquery.dropotron.js v1.4.2 | (c) n33 | n33[.]co | MIT licensed */Here we have n33[.]co with a fourth product.
11. jquery.min.js
/*! jQuery v1.11.1 | (c) 2005, 2014 jQuery Foundation, Inc. | jquery[.]org/license */Finally, we have the version of jQuery that matches Wappalyzer.
12. jquery.scrollgress.min.js
/* jquery.scrollgress vx.x | (c) n33 | n33[.]co @n33co | MIT */n33[.]co and @n33co again.
13. skel.min.js
/* skel.js v1.0 | (c) n33 | n33[.]co | MIT licensed */Yep.
14. skel-layers.min.js
/* skel-layers.js v1.0 | (c) n33 | n33[.]co | MIT licensed */You know what I'm gonna say.
NOTE: I contacted @n33co directly. They are obviously not to be blamed if attackers are abusing their tools. I wanted to ensure the readers of this blog that they are not the bad guy and were in fact very responsive to my messages, unlike a certain hosting provider. The same goes for the other developers whose tools were used in this attack.
Now that we've looked through these files, I want to gather some intelligence about the hosts.
The IP itself belongs to AS14463, TDKOM INFORMATICA LTDA., BR. As of the time of having written this post, the host was contacted via e-mail and also tagged on Twitter to bring this to their attention (Verizon support was tagged in the same thread), but after multiple contact attempts they have yet to respond. Other sources of intelligence (urlquery, VirusTotal, Google, etc.) did not reveal anything interesting about this IP, aside from Shodan which revealed a few open ports. Nothing that I am willing to touch, though, however tempting it may be.
That's honestly where my analysis ends. I reached out to a few more people involved, but there's only so much you can garner from a low-effort, cobbled-together site.
Also, this is my return post, and I'm not sure I want to strain my poor brain and fingers too much.
Stay safe.