So, let's dig into things a bit, shall we?
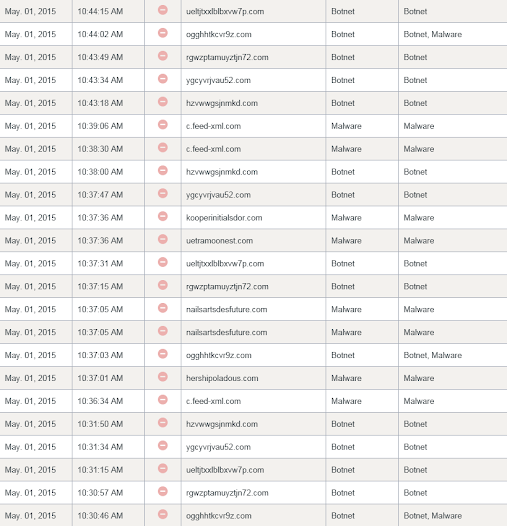
I recently had to respond to a potential botnet infection for a client. The company I work for employs OpenDNS Umbrella for managed clients, which allows us to apply their filters to all DNS queries coming from a specific WAN IP. In this particular instance, we received alerts that there were DNS queries coming from the client's WAN IP that were flagged as being related to malware/botnet (separate flags in OpenDNS Umbrella, though one domain can belong to multiple flags) activity.
You can see the requests being made in this image; there are malware requests, botnet requests, and some requests that fall into both categories.
At this point, I typically take four steps. Firstly, I immediately access the client's firewall–which we manage–and kick off a packet capture for any requests destined for the OpenDNS Umbrella botnet WAN IP, as OpenDNS functions by replying to flagged DNS queries with its sinkhole IP to block the traffic. After that, I check our managed anti-virus dashboard to see if any recent threats have been detected. Luckily for me, both actions were fruitful in this case; you will see those results below. After that, I tend to perform some passive analysis of the flagged domains online; again, read on for the results. Finally, I check the client's WAN IP on VirusTracker (https://virustracker.net) and VirusTotal (https://www.virustotal.com/) to see if there has been any history, recent or distant, of malicious activity; neither of these sites turned up anything.
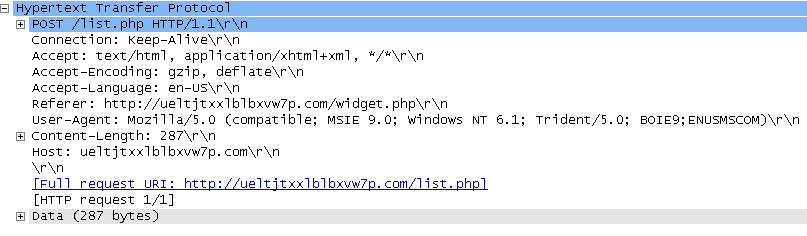
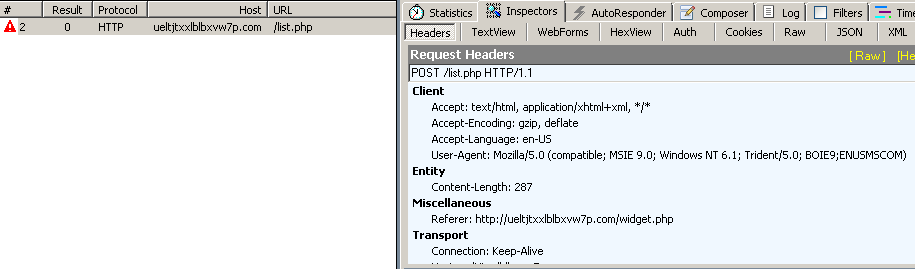
Wireshark, Network Miner, and Fiddler analysis of the single packet hex that I decided to view for this incident; unfortunately, the request I managed to capture was to one of the dead hosts (see below), so I had no response packet in the stream to analyze as well. This will wash out later on in the analysis, however.
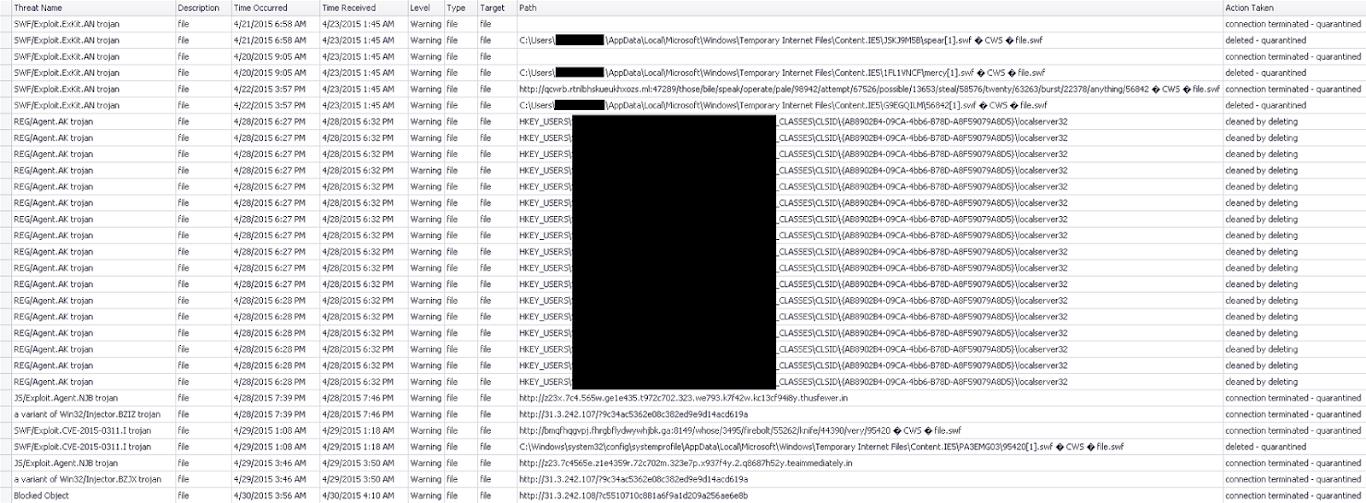
List of recent detections by ESET anti-virus from the endpoint in question (information in black has been redacted.)
• "ueltjtxxlblbxvw7p.com" (lookup failed)
• "ogghhtkcvr9z.com" (148.251.161.138) (https://www.virustotal.com/en/ip-address/148.251.161.138/information/)
• "ygcyvrjvau52.com" (lookup failed)
• "hzvwwgsjnmkd.com" (lookup failed)
• "rgwzptamuyztjn72.com" (lookup failed)
A succinct summary of lookups for the botnet queries flagged by OpenDNS; only one of the domains had an active domain registration at the time of the lookups.
At this point, I now know the IP address, MAC address, etc. of the offending host. As we manage the client's entire network, I was able to locate the host in question very quickly. That is where I am going to terminate this post. In the next post, I will cover accessing the machine, performing live Fiddler captures while the infection was active, and generating a memory dump during infection (plus analysis of said dump.)
See you soon! Be safe out there!